As of November 21, 2017, 264 data breaches affecting at least 4.4 million patients have been reported to the US Department of Health and Human Services Office for Civil Rights (OCR)i. The breaches affected physician and dental practices, hospitals, insurers, medical equipment suppliers and health systems.
There have been so many breaches that some organizations may not yet be aware of themii. For example, a clinic investigating a recent ransomware attack discovered a previously undetected breach that had occurred 15 months prior. Others may suffer the same fate—including ambulatory surgery centers (ASCs).
To date, the following types of breaches have been reported to OCR:
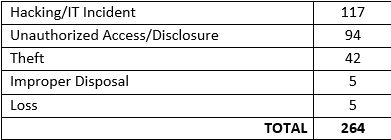
When it comes to privacy and security, small, independent providers are at the greatest risk of breach. As evidenced above, new internal threats arise every day, along with inadvertent internal staff errors. This challenge is especially onerous for smaller facilities that often lack the resources and expertise to address the constant flow of competing priorities—one of which is a risk analysis.
Perform a risk assessment
HIPAA Breach News (HBN) tracks and reports all healthcare breaches. In a post discussing recently reported breaches, HBN commented, “Many of the situations in our HIPAA breach news posts could have been avoided if a risk assessment had identified a vulnerability that was later exploited to gain access to PHI.”iii
Based on the strategy presented in the AHIMA practice brief titled “Leading the HIPAA Privacy Risk Assessment,” three reasons for performing a risk assessment are suggested:
• System weaknesses can subject the organization to liability for breach of confidentiality and invasions of privacy.
• Inappropriate uses or disclosures of information can result in negative publicity, driving patients to choose other healthcare providers.
• System flaws and loopholes can result in corruption or loss of vital data, or inappropriate alteration or manipulation of data.
With these issues in mind, ASCs can develop practical strategies for HIPAA compliance—even with limited resources.
Prioritize education and training
Education and training must be top priority. Regular training sessions keep staff abreast of privacy and security concerns. Ongoing education reduces the risk of unintentional disclosures when discussing privacy issues or leaving documents in common areas, while emphasizing the importance of observing and reporting suspicious events.
An effective education and training plan will incorporate the development, implementation, periodic review and revision of related policies and procedures. Employee orientation and annual reorientation in these areas are among the best strategies for proactively addressing problem areas.
Six policies to implement
Implementation of meaningful policies and procedures is essential to meeting your ASC’s specific needs. Using a boilerplate template designed for larger hospitals and health systems is not a wise choice. When audited, you must be able to articulate how certain practices follow established policies and procedures within your ASC. In our work with ASCs, risk analysis findings revealed the following five areas to address in developing policies and procedures.
High-profile patients
Records of high-profile patients, such as the mayor, chamber of commerce members, and others well known in the community should be kept private and confidential. One option is to assign an alias within the EHR for these individuals, and restrict access to the “need to know” list along with a “break the glass” policy to allow internal access for treatment, administrative or other specific purposes. Conduct frequent audits to determine who is accessing information and whether they have a legitimate need to know.
BYOD and remote wipe
Bring your own device (BYOD) policies and procedures are needed to define whether physicians, nurses and administrative staff are allowed to access PHI on personal devices— such as personal laptops, tablets and smartphones—and under what parameters. The policies should spell out requirements for device encryption and whether employees are required to sign a remote wipe policy in case a phone is lost or stolen. Another option is to issue phones internally to staff members. While this may seem cost prohibitive for small providers, it may be well worth the investment to protect PHI.
Confidentiality, storage, destruction and disposal of PHI
Proper retention and destruction of PHI in any format—paper and electronic—is critical. Every healthcare organization, regardless of size, must have a retention and disposal program in place—a core principle of information governance. And with hacking, phishing and ransomware attacks on the rise, data backup is more important than ever.
Encryption
As evidenced by the increase in remote data breaches, healthcare organizations are realizing the need for encryption as a requirement to protect PHI. Lack of awareness is no excuse. Encryption is a must.
Physical security
Physical security includes the use of alarm systems along with proper storage and access to PHI. For example, breaches have occurred when an unencrypted laptop was accessed via an unlocked office and when paper files were stored in an employee break area with unrestricted access. Diligence is required to protect PHI, especially when providers have limited space and storage issues.
Job descriptions
Privacy and security job descriptions must fully document and identify who will assume privacy and security roles, and specify their responsibilities. It is not uncommon for employees to have dual roles, such as an IT director who is also the security officer, or an HIM or compliance director who serves as the privacy officer. In such cases, job descriptions should specify roles and responsibilities.
Take a proactive approach
As incidents of PHI hacking increase, ensuring routine auditing and monitoring is imperative to reveal in advance who might be accessing information. A proactive approach is best practice versus waiting until a potential problem arises. In the long run, it’s much more efficient and cost effective to spend resources on preventing a breach rather than investigating, reporting and recovering from an event.
ASCs should engage in risk analysis as a proactive means of breach prevention. This entails regular review of administrative processes, physical safeguards and technical capabilities. Routine risk analysis is not an option. It’s a requirement.
i https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf
ii http://www.healthcareitnews.com/news/atlanta-clinic-finds-15-month-breach-during-investigation-separate-ransomware-attack
iii https://www.hipaajournal.com/category/hipaa-breach-news/
About the Author:
As President of Primeau Consulting Group, Debra (Debi) Primeau has over 35 years of experience in Health Information Management and Health Information Technology as an Executive Consultant, IS Director, and HIM Director. Debi leads Primeau Consulting Group as HIM and HIT Practice Leader working with other HIM and HIT professionals in the industry to bring superior consulting services to the healthcare industry. Previously, Debi has worked with various HIM consulting companies as the VP of HIM Services, Compliance of Privacy and Security, as well being responsible for developing and implementing clinical documentation improvement programs, in addition to developing and providing education and training programs.
She is a graduate of the University of Phoenix with a degree in business management, in addition to a Masters degree in organizational management. She is the Past President for the California Health Information Association (CHIA), recipient of the Distinguished Member Award, serves on several AHIMA committees, has given numerous presentations and written for HIM and affiliated healthcare publications.
